With the growing adoption of Google Cloud technologies, knowledge of security has gained paramount importance over the years. It is crucial to understand the technologies, policies, processes, and controls to secure Google Cloud Platform applications. Cloud technologies and security go hand in hand, as cybersecurity threats can invade your applications and affect your business's confidentiality, integrity, and availability. Security is a shared responsibility of the application owner and cloud provider, and it's essential to understand how to build a robust security model. We have listed 10 security best practices to help keep your cloud environment secure.
Understand Your Cloud Locations and Services
Understanding your cloud locations and services is a critical best practice to keep your applications secure. Google Cloud services and products are built on top of the core infrastructure, which has in-built security features like access control, segmentation, and data control. However, you need to know how your data is stored, encrypted, and managed to ensure your information is secure.
Google Cloud has VPCs, or Virtual Private Cloud, which is an on-demand pool of shared resources. VPC are isolated from each other and can talk through VPC peering. You can control all network ingress, inbound, and egress outbound traffic to any resource via simple firewall rules. When designing a robust security model, the first step is knowing how your applications are hosted and what Google provides all security services and products.
Google's data loss prevention API helps you discover, classify, and protect your sensitive data. It's a fully managed service that inspects your structured and unstructured data, helping you gain insight and reduce any risk to your data applications.
Understand Your External and Internal Security Threats
Understanding and being aware of your internal and external threats can help you stay proactive and keep your applications secure. Hazards can be present anywhere, and it's useful to understand the STRIDE Threat Model to keep on top of all the threats your applications can face on Google Cloud.
STRIDE stands for spoofing, tampering, repudiation, denial of service, and elevation of privilege. The infographic below explains each of these threats.
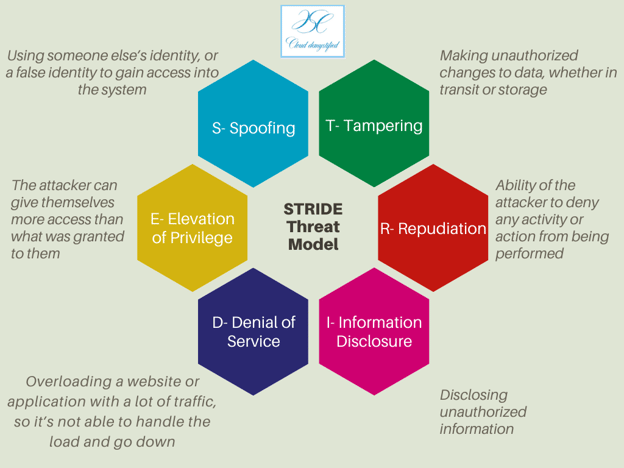
Google Cloud Armor helps protect your applications against denial of services and has built-in security against L3 and L4 DDoS attacks. Leveraging this for your applications on Google Cloud can help provide an additional security layer against any of the threats outlined in the STRIDE model.
Identity and Access Management Control
IAM is a framework of policies and processes defined by the cloud provider to make sure users have appropriate permissions to access resources, applications, and data on the cloud. IAM helps secure the data, prevent unwanted threats, and ensure all the users have the right amount of access to get their work done.
Google Cloud Platform has many services and products to protect users and applications by understanding, managing, and controlling access.
All resources on Google Cloud are managed hierarchically and are grouped into four parts- organization, folders, projects, and resources. For example, a company using Google Cloud is the top node, followed by folder, project, and resources. Each resource has only one parent, and children inherit the policies of their parents. So, by default, policies set at the organization node are inherited by all the folders, projects, and resources under that organization. Resource Manager lets you centrally manage these resources by projects, folder, and organization.
A fundamental way to filter out unwanted users is to set up a robust authentication framework, which gives access only to the users who can validate their identity. Google Authenticator lets you do that without having to put in any extra effort. However, cloud Identity provides additional solutions to secure your account, device, and workspace with advanced protection and password-vaulted applications. You can choose from various solutions like Single Sign-on (one-click access to applications), multi-factor authentication (using two or more devices to validate identity), and endpoint management.
To guard access to your applications, you can use Identity-Aware Proxy. You can verify who is trying to access your application and grant access accordingly. This move helps implement a zero-trust model, along with centralized access control. IAP can protect access to applications hosted on Google Cloud, any other cloud, or even on-premise infrastructure.
Here are some of the IAM best practices that you can follow to keep the data in your applications secure.
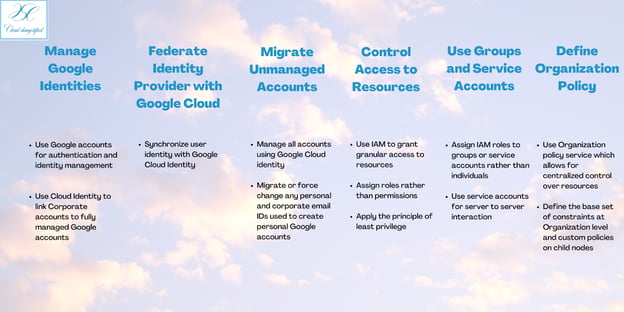
Active Monitoring
Actively monitoring your environment and application helps discover potential intruders who may be lurking around and targeting your applications' data. Knowing who is accessing your data and monitoring any suspicious activity can help you stay proactive and keep your applications secure.
Google Cloud Monitoring, formerly known as Stackdriver Monitoring, helps monitor, troubleshoot, and improve your applications' performance on Google Cloud. It's a fully managed, scalable service that provides easy-to-view and access dashboards with several performance indicators and notifications/alerts.
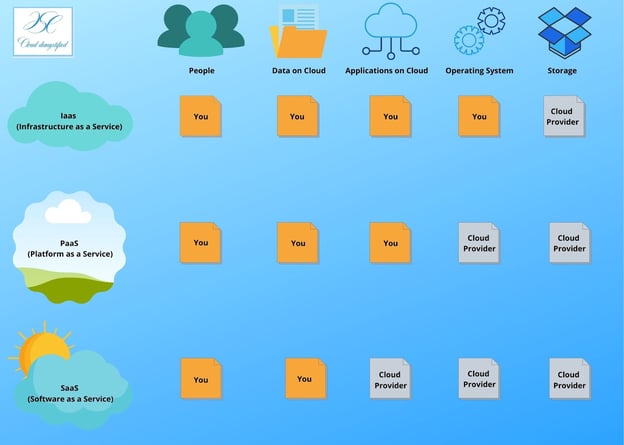
Understand the Shared Responsibility Model
Google Cloud Platform provides various services ranging from highly managed (Function as a Service) to highly customizable (Infrastructure as a Service). Each service comes with its security responsibility model. The following diagram shows Google's Compute offerings, which you can use to run your applications.
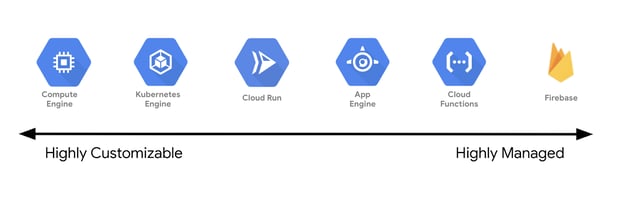
Knowing and understanding these services would act as a stepping stone to design the shared responsibility model. Like Cloud Functions or Firebase, highly managed offerings have more built-in security than highly customizable offerings that provide more flexibility to the users. The following diagram illustrates the shared security model based on the type of service offering to run your applications.
Keep Your Data Encrypted
When all data is converted into a secret code or encrypted, the information's true meaning is hidden. Encryption ensures that the data is not accessible by anyone other than the ones allowed to access it.
Google Cloud Platform encrypts data at rest by default, which means it encrypts the data stored by you with no additional action required. Data is encrypted before the application writes it to your disk. A set of master keys encrypt each key and applies to almost all data you have on the cloud.
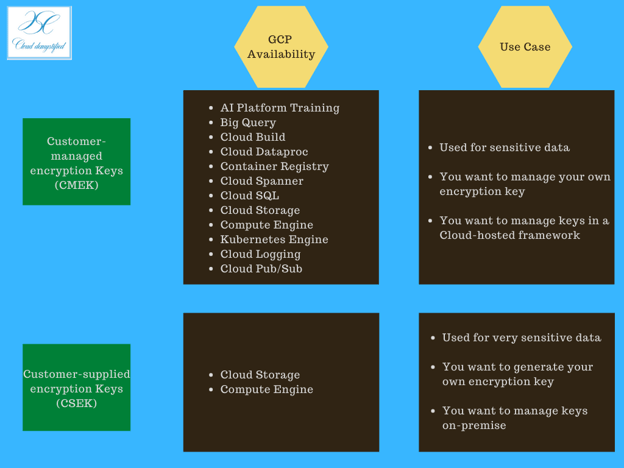
If you have more sensitive data, you can manage your encryption key. For this, you have customer-supplied, and customer-managed keys. The below image compares these two options to help you make the right choice.
Thorough Vulnerability and Penetration Testing
This complicated term means putting on the hat of the attacker and thinking like one. By this method, the organizations or the cloud service providers attack their infrastructure to test the stability and discover vulnerabilities allowing them to catch and fix vulnerabilities before any outsider can find them.
Google Cloud Platform provides a Web Security Scanner as a part of the Security Command Center to detect critical vulnerabilities in your applications, even before its deployment. It identifies vulnerabilities in your App Engine, Kubernetes Engine, and Compute Engine instances and lets you stay ahead in the security game.
Establish and Manage Firewalls
A firewall is simply a wall or barrier attached to the system to prevent intruders from getting inside. In cloud computing, they are rules attached to systems to block unauthorized access while allowing outward communication.
Setting security rules on incoming and outgoing traffic would help establish a barrier between the intruders and the system by filtering traffic inside and blocking outsiders from gaining unwanted access to the data.
To allow or deny connections from your virtual machine (VM), you can apply firewall rules in your Virtual Private Cloud (VPC). Within the configuration, you can set, identify and enforce VPC firewall rules allowing you to protect your applications regardless of their configuration and operating system, even if they have not started up.
Manage and Institute Cloud Security Guidelines
Instituting and managing security best practices and guidelines for the organization is essential to ensure your applications' safety. It's necessary to streamline processes to ensure the staff, stakeholders, partners, and leadership are on the same page.
Google Cloud has many security partner products you can leverage for all your security needs. Apart from that, they have several infrastructures, data protection, logging, and compliance partners who can guide you and your organization to formulate the best guidelines for your applications. To secure your applications and scan non-compliance resources in your infrastructure, you can leverage open-source tools like Forseti and Config Validator.
Here's a snapshot of some of the partners who can guide you in your security needs on Google Cloud. You can view the complete list under the resources section of this article.

Train Your Staff
The last but critical best practice is to keep your staff up to date on security threats and best practices. Any security measure is of no use if the organization does not follow it. It's of paramount importance to ensure everyone is aware of security threats and follow the organization's best practices instituted. Google Cloud provides training, whitepapers, articles, and support to ensure compliance with all the industry standards to keep your applications secure.
Visual Learner? Resource for You.
Extra Credit
Here are some resources that you can use to understand cloud security better and design a robust security framework for your applications on the Google Cloud Platform: